A Comprehensive Guide to Protect APK Files from Reverse Engineering
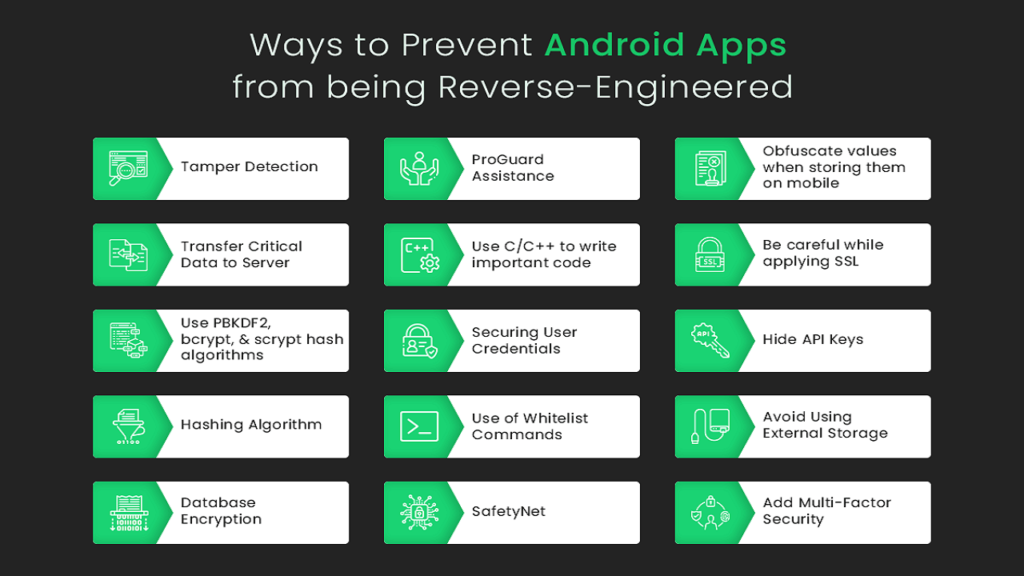
How to Protect APK Files from Reverse Engineering educate protecting your APK files from reverse engineering is crucial to safeguard your intellectual property and user data. In the world of Android app advancement, protecting APK files from reverse engineering is essential. Reverse engineering permits malevolent users to decompile and comprehend your app’s source code. This can prompt unapproved access, information robbery, and in any event, cloning of your app. Consequently, executing solid safety efforts is fundamental. This article will direct you through different techniques to shield your APK files.
Reverse engineering includes decompiling an APK document to get to its source code. Devices like APKTool and JADX make this cycle somewhat simple. By decompiling, assailants can concentrate on the code, track down weaknesses, and take advantage of them. They can likewise change the app and reallocate it as their own. Consequently, understanding the rudiments of reverse engineering is the most vital phase in protecting your APK files.
More Queries: How to Optimize APK File Size
Importance of Code Obfuscation:
One viable method for protecting your APK files is through code confusion. Muddling changes your code into a more complicated and less lucid structure. This makes it hard for aggressors to figure out the rationale of your application. ProGuard is a famous apparatus for code obscurity in Android improvement. It jumbles your code as well as eliminates unused code and decreases the size of your APK record.
Using ProGuard for Obfuscation:
ProGuard is coordinated into Android Studio, making it simple to utilize. To empower ProGuard, you want to set the minifyEnabled property to valid in your build.gradle document. Additionally, you can redo ProGuard rules to suit your requirements. While ProGuard gives essential obscurity, there are other high level apparatuses like DexGuard and R8 that proposition improved protection.
Encryption Techniques:
Encryption is one more fundamental strategy to protect your APK files. By scrambling touchy information, you can ensure that regardless of whether assailants decompile your APK, they can’t get to basic information. There are different encryption methods accessible, like AES (High level Encryption Standard) and RSA (Rivest-Shamir-Adleman). Carrying out encryption requires cautious wanting to ensure that keys are put away safely and that presentation isn’t essentially affected.
Securing API Keys:
Programming interface keys are frequently designated by aggressors since they give admittance to backend administrations. To protect your Programming interface keys, you ought to stay away from hardcoding them in your source code. All things considered, use climate factors or secure stockpiling arrangements like Android Keystore. Additionally, you can execute the Programming interface key turn and check to distinguish and answer unapproved use.
Utilizing ProGuard and R8:
While ProGuard offers fundamental obscurity, R8 gives further developed highlights. R8 is a substitution for ProGuard in the Android construct process. It offers better execution and extra jumbling strategies. By utilizing R8, you can additionally protect your APK files from reverse engineering. Arranging R8 is like ProGuard, and it tends to be empowered by setting the minifyEnabled property to be valid in your build.gradle record.
Applying Resource Obfuscation:
Resource files, like XML formats and pictures, can likewise be designated by aggressors. Resource obscurity devices, such as ReSa (Resource Shrinker and Obfuscator), can assist with protecting these files. By muddling resource names and ways, you make it harder for aggressors to comprehend and change your app’s resources. This adds a layer of protection to your APK files.
Implementing Integrity Checks:
Honesty checks ensure that your APK document has not been altered. By carrying out checksums or advanced marks, you can confirm the uprightness of your APK record. If the document has been changed, the checksums won’t coordinate, showing a potential security break. Android offers worked in help for uprightness takes a look at using the Mark consent and APK Mark Plan V2.
Using Anti-Tamper Techniques:
Alter strategies can keep aggressors from changing your APK document. These procedures include adding code that checks for changes in your app’s double. If any progressions are identified, the app can end or set off a security reaction. Libraries like Carefully Designed and DexProtector offer enemies of alter highlights that can be coordinated into your app.
Leveraging Native Code:
Local code, written in C or C++, is more earnest to reverse design contrasted with Java or Kotlin code. By moving basic pieces of your application rationale to local code, you can expand the trouble for assailants. The Android NDK (Local Advancement Unit) permits you to incorporate local code into your app. However, this approach requires extra advancement exertion and cautious thought of execution suggestions.
Utilizing License Verification:
Permit checks can help protect your app from unapproved dispersion. Google Play gives a Permitting Confirmation Library (LVL) that permits you to take a look at the permit status of your app. By incorporating permit confirmation, you can ensure that main users who have bought or downloaded your app from approved sources can utilize it. This adds one more layer of protection against reverse engineering.
Implementing Security Best Practices:
In addition to the techniques referenced above, it is fundamental to follow general security best practices. These incorporate keeping your improvement climate secure, routinely refreshing conditions, and directing intensive code surveys. By embracing a security-first approach, you can lessen the gamble of your APK files being reverse-designed.
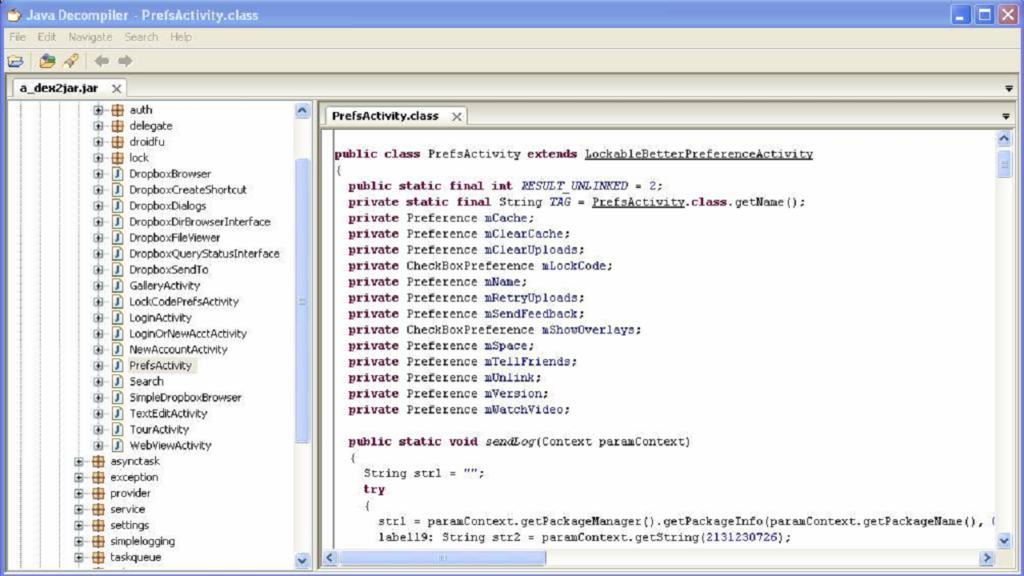
Monitoring and Responding to Threats:
Observing your app for indications of reverse engineering and other security dangers is urgent. Executing logging and examination can assist you with recognizing dubious exercises. Additionally, setting up alarms for strange examples can empower you to respond rapidly to possible dangers. Routinely evaluating security logs and remaining refreshed on the most recent security patterns will assist you with remaining in front of aggressors.
Conclusion
How to Protect APK Files from Reverse Engineering Download is a persistent cycle that requires a mix of techniques. Code muddling, encryption, getting Programming interface keys, and utilizing hostile to alter techniques are a portion of the key methodologies. Additionally, utilizing local code, applying resource confusion, and executing permit checks can upgrade security. By taking on these practices and remaining cautious, you can essentially decrease the gamble of your APK files being reverse-designed. Keep in mind, that security is not a one-time exertion but a continuous obligation to protect your app and its users.